Steve Blank's Blog, page 2
October 8, 2024
How Saboteurs Threaten Innovation–and What to Do About It
This article first appeared in First Round Review.
“Only the Paranoid Survive”
Andy Grove – Intel CEO 1987-1998
I just had an urgent “can we meet today?” coffee with Rohan, an ex-student. His three-year-old startup had been slapped with a notice of patent infringement from a Fortune 500 company. “My lawyers said defending this suit could cost $500,000 just for discovery, and potentially millions of dollars if it goes to trial. Do you have any ideas?”
The same day, I got a text from Jared, a friend who’s running a disruptive innovation organization inside the Department of Defense. He just learned that their incumbent R&D organization has convinced leadership they don’t need any outside help from startups or scaleups.
Sigh….
Rohan and Jared have learned three valuable lessons:
Only the paranoid survive (as Andy Grove put it)If you’re not losing sleep over who wants to kill you, you’re going to die.The best fight is the one you can avoid.It’s a reminder that innovators need to be better prepared about all the possible ways incumbents sabotage innovation.
Innovators often assume that their organizations and industry will welcome new ideas, operating concepts and new companies. Unfortunately, the world does not unfold like business school textbooks.
Whether you’re a new entrant taking on an established competitor or you’re trying to stay scrappy while operating within a bigger company here’s what you need to know about how incumbents will try to stand in your way – and what you can do about it.
 Entrepreneurs versus Saboteurs
Entrepreneurs versus Saboteurs
Startups and scaleups outside of companies or government agencies want to take share of an existing market, or displace existing vendors. Or if they have a disruptive technology or business model, they want to create a new capability or operating concept – even creating a new market.
As my student Rohan just painfully learned, the incumbent suppliers and existing contractors want to kill these new entrants. They have no intention of giving up revenue, profits and jobs. (In the government, additional saboteurs can include Congressional staffers, Congressman and lobbyists, as these new entrants threaten campaign contributions and jobs in local districts.)
Intrapreneurs versus Saboteurs
Innovators inside of companies or government agencies want to make their existing organization better, faster, more effective, more profitable, more responsive to competitive threats or to adversaries. They might be creating or advocating for a better version of something that exists. Or perhaps they are trying to create something disruptive that never existed before.
Inside these commercial or government organizations there are people who want to kill innovation (as my friend Jared just discovered). These can be managers of existing programs, or heads of engineering or R&D organizations who are feeling threatened by potential loss of budget and authority. Most often, budgets and headcount are zero-sum games so new initiatives threaten the status quo.
Leaders of existing organizations often focus on the success of their department or program rather than the overall good of the organization. And at times there are perverse incentives as some individuals are aligned with the interests of incumbent vendors rather than the overall good of the company or government agency.
How Do incumbents Kill Innovation?
Rohan and Jared were each dealing with one form of innovation sabotage. Incumbents use a variety of ways to sabotage and kill innovative ideas inside of organizations and outside new companies. And most of the time innovators have no idea what just hit them. And those that do – like Rohan and Jared – have no game plan in place to respond.
Here are the most common methods of sabotage that I’ve seen, followed by a few suggestions on how to prepare and defend against them.
Founders and Innovators should expect that existing organizations and companies will defend their turf – ferociously.
Common ways incumbents kill innovation in both commercial markets and government agencies.Create career FUD (fear, uncertainty and doubt). Positioning the innovative idea, product or service as risk to the career of whoever adopts or champions it.Emphasize the risk to existing legacy investments, like the cost of switching to the new product or service or highlighting the users who would object to it.Claim that an existing R&D or engineering organization is already doing it (0r can do it better/cheaper.)Create innovation theater by starting internal innovation programs with the existing staff and processes.Set up committees and advisory boards to “study” the problem. Appoint well respected members of the status quo.Poison funding for internal initiatives. Claiming that you’ll have to kill important program x or y to pay for the new initiative. Or funding the demo of the new idea and then “slow-walk” the budget for scale.File Lawsuits/Protests against winners of contracts.Use patents as a weapon. Filing patent infringement lawsuits – whether true or not. Try to invalidate existing patents – whether true or not.Claim that employees have stolen IP from their previous employer.File HR Complaints against internal intrapreneurs for cutting corners or breaking rules.Isolate senior leadership from the innovators inside the organization via reporting hierarchy and controlling information about alternatives.Object to structures and processes for the rapid adoption of new technologies. Treat innovation and execution as the same processes. Lack tolerance for failure at innovation. Do not cultivate a culture of urgency. Don’t offer a a structured career path for innovators.Lock-up critical resources, like materials, components, people, law firms, distribution channels, partners and make them unavailable to innovation groups/startups.Control industry/government standards to ensure that they are lock-in’s for incumbents.Acquire a startup and shut it down or bury its productPoach talent from an innovation organization or company by convincing talent that the innovation effort won’t go anywhere.Influence “independent” analysts, market research firms with “research” contracts to prove that the market is too small.Confuse buyers and senior leadership by preannouncing products or products that never ship – vaporware.Bundle products (Microsoft Office)Long term lock-in contracts for commercial customers or sole-source for government programs (e.g. F-35).How incumbents kill startups in government marketsFile contract appeals or protests, creating delays that burn cash for new entrants.File Inspector General (IG) complaints, claiming innovators are cutting corners, breaking rules or engaging in illegal hiring and spending. If possible, capture these IG offices and weaponize them against innovators.Hijack the acquisition system by creating requirements written for incumbents, while setting unnecessary standards, barriers and paperwork for new entrants. Ignore requirements to investigate alternate suppliers and issue contracts to the incumbents.Revolving door. The implicit promise of jobs to government program executives and managers and the implicit promise of jobs to congressional staffers and congressmen.Lobbying. Incumbents have dedicated staffs to shape requirements and budgets for their products, as well as dedicated staff for continual facetime in Washington. They are experts at managing the POM, PPBE, House and Senate Armed Services Committees and appropriations committees.Create career risks for innovators attempting to gain support outside of official government channels, penalizing unofficial contacts with members of Congress or their staffs.Create Proprietary interfacesWeaponize security clearances, delaying or denying access to needed secure information, or even pulling your, or your company’s clearance.How incumbents kill startups in commercial markets.Rent Seeking via regulatory bodies (e.g. FCC, SEC, FTC, FAA, Public Utility, Taxi/Insurance Commissions, School Boards, etc, …) Use government regulation to keep out new entrants who have more innovative business models (or delay them so the incumbents can catch up).Rent Seeking via local, state and federal laws (e.g. occupational licensing, car dealership laws, grants, subsidies, or tariff protection). Use arguments – from public safety, to lack of quality, or loss of jobs – to lobby against the new entrants.Rent Seeking via courts to tie up and exhaust a startup’s limited financial resources.Rent Seeking via proprietary interfaces (e.g. John Deere tractor interfaces…)Poison startup financing sources. Telling VCs the incumbents already own the market. Tell Government funders the company is out of cash.Legal kickbacks, like discounts, SPIFs, Co-advertising (e.g. Intel and Microsoft for x86 processors/Windows).State Attorney General complaints to tie up startup resourcesCreate fake benchmark groups or greenwash groups to prove existing solution is better or that new solution is worse.Innovators Survival Checklist
There is no magic bullet I could have offered Rohan or Jared to defend against every possible move an incumbent might make. However, if they had realized that incumbents wouldn’t welcome them, they (and you) might have considered the suggestions below on how to prepare for innovation saboteurs.
In both government and commercial markets:
Map the order of battle. Understand how the money flows and who controls budget, headcount and organizational design. Understand who has political, regulator, leadership influence and where they operate.Understand saboteurs and their motivation. Co-opt them. Turn them into advocates – (this works with skeptics). Isolate them – with facts. Get them removed from their job (preferably by promoting them to another area.)Build an insurgent team. A technologist, visionary, champion, allies, proxies, etc. The insurgency grows over time.Avoid publicly belittling incumbents. Do not say, “They don’t get it.” That will embarrass, infuriate and ultimately motivate them to put you out of business.Avoid early slideware. Instead focus on delivering successful minimal viable products which demonstrate feasibility and a validated requirement.Build evidence of your technical, managerial and operational excellence. Build Minimal Viable Products (MVPs) that illustrate that you understand a customer or stakeholders problem, have the resources to solve it, and a path to deployment.If possible, communicate and differentiate your innovation as incremental innovation. Point out that over time it’s disruptive.Go after rapid scale of a passionate customer who values the disruption e.g. INDOPACOM; or Uber and Airbnb, Tesla in the commercial worldAlly with larger partners who see you as a way to break the incumbents’ lock on the market. i.e. Palantir and the intelligence agencies versus the Army and in industry, IBM’s i2, / Textron Systems Overwatch.In commercial markets:Figure out an “under the radar” strategy that doesn’t attract incumbents’ lawsuits, regulations or laws when you have limited resources to fight back.Patent strategy. Build a defensive patent portfolio and strategy? And consider an offensive one, buying patents you think incumbents may infringe.Pick early markets where the rent seekers are weakest and scale. For example, pick target markets with no national or state lobbying influence. i.e. Craigslist versus newspapers, Netflix versus video rental chains, Amazon versus bookstores, etc.When you get scale and raise a large financing round, take the battle to the incumbents. Strategies at this stage include hiring your own lobbyists, or working with peers in your industry to build your own influence and political action groups.Jared is still trying to get senior leadership to understand that the clock is ticking, and internal R&D efforts and current budget allocation won’t be sufficient or timely. He’s building a larger coalition for change, but the inertia for the status quo is overwhelming.
Rohan’s company was lucky. After months of scrambling (and tens of thousands of dollars), they ended up buying a patent portfolio from a defunct startup and were able to use it to convince the Fortune 500 company to drop their lawsuit.
I hope they both succeed.
What have you found to be effective in taking on incumbents?
October 5, 2024
What Does Product Market Fit Sound Like? This.
I got a call from an ex-student asking me “how do you know when you found product market fit?”
There’s been lots of words written about it, but no actual recordings of the moment.
I remembered I had saved this 90 second, 26 year-old audio file because this is when I knew we had found it at Epiphany.
The speaker was the the Chief Financial Officer of a company called Visio, subsequently acquired by Microsoft
I played it for her and I think it provided some clarity.
https://steveblank.com/wp-content/uploads/2024/10/NIEL.wavIt’s worth a listen.
If you can’t hear the audio click here
September 17, 2024
How To Find Your Customer In the Dept of Defense – The Directory of DoD Program Executive Offices
Finding a customer for your product in the Department of Defense is hard: Who should you talk to? How do you get their attention?

Looking for DoD customers
How do you know if they have money to spend on your product?
It almost always starts with a Program Executive Office.
The Department of Defense (DoD) no longer owns all the technologies, products and services to deter or win a war – e.g. AI, autonomy, drones, biotech, access to space, cyber, semiconductors, new materials, etc.
Today, a new class of startups are attempting to sell these products to the Defense Department. Amazingly, there is no single DoD-wide phone book available to startups of who to call in the Defense Department.
So I wrote one.
Think of the PEO Directory linked below as a “Who buys in the government?” phone book.
The DoD buys hundreds of billions of dollars of products and services per year, and nearly all of these purchases are managed by Program Executive Offices. A Program Executive Office may be responsible for a specific program (e.g., the Joint Strike Fighter) or for an entire portfolio of similar programs (e.g., the Navy Program Executive Office for Digital and Enterprise Services). PEOs define requirements and their Contracting Officers buy things (handling the formal purchasing, issuing requests for proposals (RFPs), and signing contracts with vendors.) Program Managers (PMs) work with the PEO and manage subsets of the larger program.
Existing defense contractors know who these organizations are and have teams of people tracking budgets and contracts. But startups? Most startups don’t have a clue where to start.
This is a classic case of information asymmetry and it’s not healthy for the Department of Defense or the nascent startup defense ecosystem.
That’s why I put this PEO Directory together.
This first version of the directory lists 75 Program Executive Offices and their Program Executive Officers and Program/Project Managers.
Each Program Executive Office is headed by a Program Executive Officer who is a high ranking official – either a member of the military or a high ranking civilian – responsible for the cost, schedule, and performance of a major system, or portfolio of systems, some worth billions of dollars.
Below is a summary of 75 Program Executive Offices in the Department of Defense.
You can download the full 64-page document of Program Executive Offices and Officers with all 602 names here.
 Caveats
Caveats
Do not depend on this document for accuracy or completeness.
It is likely incomplete and contains errors.
Military officers typically change jobs every few years.
Program Offices get closed and new ones opened as needed.
This means this document was out of date the day it was written. Still it represents an invaluable starting point for startups looking to work with DoD.
How to Use The PEO Directory As Part of A Go-To-Market Strategy
While it’s helpful to know what Program Executive Offices exist and who staffs them, it’s even better to know where the money is, what it’s being spent on, and whether the budget is increasing, decreasing, or remaining the same.
The best place to start is by looking through an overview of the entire defense budget here. Then search for those programs in the linked PEO Directory. You can get an idea whether that program has $ Billions, or $ Millions.
Next, take a look at the budget documents released by the DoD Comptroller –
particularly the P-1 (Procurement) and R-1 (R&D) budget documents.
Combining the budget document with this PEO directory helps you narrow down which of the 75 Program Executive Offices and 500+ program managers to call on.
With some practice you can translate the topline, account, or Program Element (PE) Line changes into a sales Go-To-Market strategy, or at least a hypothesis of who to call on.
Armed with the program description (it’s full of jargon and 9-12 months out of date) and the Excel download here and the Appendix here –– you can identify targets for sales calls with DoD where your product has the best chance of fitting in.
The people and organizations in this list change more frequently than the money.
Knowing the people is helpful only after you understand their priorities — and money is the best proxy for that.
Future Work
Ultimately we want to give startups not only who to call on, and who has the money, but which Program Offices are receptive to new entrants. And which have converted to portfolio management, which have tried OTA contracts, as well as highlighting those who are doing something novel with metrics or outcomes.
Going forward this project will be kept updated by the Stanford Gordian Knot Center for National Security Innovation.
In the meantime send updates, corrections and comments to [email protected]
Credit Where Credit Is Due
Clearly, the U.S. government intends to communicate this information. They have published links to DoD organizations here, even listing DoD social media accounts. But the list is fragmented and irregularly updated. Consequently, this type of directory has not existed in a usable format – until now.
August 13, 2024
Security Clearances at the Speed of Startups
Imagine you got a job offer from a company but weren’t allowed to start work – or get paid – for almost a year. And if you can’t pass a security clearance your offer is rescinded. Or you get offered an internship but can’t work on the most interesting part of the project. Sounds like a nonstarter. Well that’s the current process if you want to work for companies or government agencies that work on classified programs.
One Silicon Valley company, Palantir, is trying to change that and shorten the time between getting hired and doing productive work. Here’s why and how.
Over the last five years more of my students have understood that Russia’s brutal war in Ukraine and strategic competition with the People’s Republic of China mean that the world is no longer a stable and safe place. This has convinced many of them to work on national security problems in defense startups.
However, many of those companies and government agencies require you to work on projects with sensitive information the government wants to protect. These are called classified programs. To get hired, and to work on them, you need to first pass a government security clearance. (A security clearance is how the government learns whether you are trustworthy enough to keep secrets and not damage national security.)
For jobs at most defense startups/contractors or national security agencies, instead of starting work with your offer letter, you’d instead receive a “conditional” job offer – that’s a fancy way to say, “we want you to work here, but you need to wait 3 to 9 months without pay until you start, and if you can’t pass the security clearance we won’t hire you.” That’s a pretty high bar for students who have lots of other options for where to work.
Types of Security Clearances
The time it takes for the clearance process depends on the thoroughness and how deeply the government investigates your background. That’s directly related to how classified will be the work you will be doing. The three primary levels of classification (from least to greatest) are Confidential, Secret, and Top Secret.  The type and depth of background investigations to get a security clearance depends on what level of classified information you will be working with. For example, if you just need access to Confidential or Secret material they would do a National Agency Check with Law and Credit (NACLC). The government will look at the FBI’s criminal history repository, do a credit check, and a check with your local law enforcement agencies. This can take a relatively short time (~3 months).
The type and depth of background investigations to get a security clearance depends on what level of classified information you will be working with. For example, if you just need access to Confidential or Secret material they would do a National Agency Check with Law and Credit (NACLC). The government will look at the FBI’s criminal history repository, do a credit check, and a check with your local law enforcement agencies. This can take a relatively short time (~3 months).
On the other hand if you’re going to work on a Top Secret/SCI project, this requires a more extensive (and much longer ~6-9 months) background check called a Single Scope Background Investigation (SSBI). Some types of clearances also require you to take a polygraph (lie-detector) test.
How Does the Government “Clear” you?
The National Background Investigation Services (NBIS) is the government agency that will investigate your background. They will ask about your:
Palantir’s Accelerated Student Clearance Plan
Palantir wants their interns and new hires to hit the ground running and work on the toughest and most interesting government problems from day one. However, these types of problems require having a security clearance. The problem is that today, all companies start an application for a security clearance the day you show up for work.
Palantir’s idea? If you get an internship or full-time offer from Palantir while you’re still in school, they will immediately employ you as a contractor. This will let them start your security clearance process while in school before you show up for work. That means you will be cleared ~9 months later in time for your first day on the job. Think of this like a college early admissions program. (If you’re interning, Palantir will hold your clearance for you if you come back to Palantir the following year.)
Why Do This?
Obviously this is a long-term strategic investment in Palantir’s college talent, but it also affects the entire defense ecosystem – to create a broader team of America’s best engineers who are able to support our country’s most critical missions. And they are encouraging other Defense Tech companies to implement a similar program.
I think it’s a great idea.
Now what are the other innovative ideas Silicon Valley can do to attract a national security workforce?
July 30, 2024
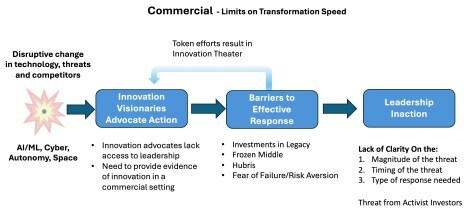
Why Large Organizations Struggle With Disruption, and What to Do About It
Seemingly overnight, disruption has allowed challengers to threaten the dominance of companies and government agencies as many of their existing systems have now been leapfrogged. How an organization reacts to this type of disruption determines whether they adapt or die.
 I’ve been working with a large organization whose very existence is being challenged by an onslaught of technology (AI, autonomy, quantum, cyberattacks, access to space, et al) from aggressive competitors, both existing and new. These competitors are deploying these new technologies to challenge the expensive (and until now incredibly effective) legacy systems that this organization has built for decades. (And they are doing it at speed that looks like a blur to this organization.) But the organization is also challenged by the inaction of its own leaders, who cannot let go of the expensive systems and suppliers they built over decades. It’s a textbook case of the Innovators Dilemma.
I’ve been working with a large organization whose very existence is being challenged by an onslaught of technology (AI, autonomy, quantum, cyberattacks, access to space, et al) from aggressive competitors, both existing and new. These competitors are deploying these new technologies to challenge the expensive (and until now incredibly effective) legacy systems that this organization has built for decades. (And they are doing it at speed that looks like a blur to this organization.) But the organization is also challenged by the inaction of its own leaders, who cannot let go of the expensive systems and suppliers they built over decades. It’s a textbook case of the Innovators Dilemma.
In the commercial world creative destruction happens all the time. You get good, you get complacent, and eventually you get punched in the face. The same holds true for Government organizations, albeit with more serious consequences.
This organization’s fate is not yet sealed. Inside it, I’ve watched incredibly innovative groups create autonomous systems and software platforms that rival anything a startup is doing. They’ve found champions in the field organizations, and they’ve run experiments with them. They’ve provided evidence that their organization could adapt to the changing competitive environment and even regain the lead. Simultaneously, they’ve worked with outside organizations to complement and accelerate their internal offerings. They’re on the cusp of a potential transformation – but leadership hesitates to make substantive changes.
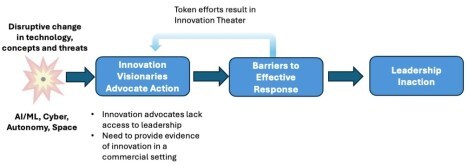
The “Do Nothing” Feedback Loop
I’ve seen this play out time and again in commercial and government organizations. There’s nothing more frustrating for innovators than to watch their organization being disrupted while its senior leaders hesitate to take more than token actions. On the other hand, no one who leads a large organization wants it to go out of business. So, why is adapting to changed circumstances so hard for existing organizations?
The answer starts at the top. Responding to disruption requires action from senior leadership: e.g. the CEO, board, Secretary, etc. Fearful that a premature pivot can put their legacy business or forces at risk, senior leaders delay deciding – often until it’s too late.
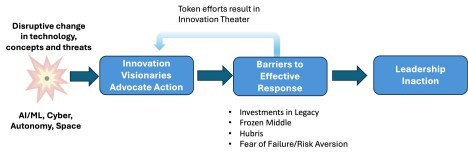
My time with this organization helped me appreciate why adopting and widely deploying something disruptive is difficult and painful in companies and government agencies. Here are the reasons:
Disconnected Innovators – Most leaders of large organizations are not fluent in the new technologies and the disruptive operating concepts/business models they can create. They depend on guidance from their staff and trusted advisors – most of whom have been hired and promoted for their expertise in delivering incremental improvements in existing systems. The innovators in their organization, by contrast, rarely have direct access to senior leaders. Innovators who embrace radically new technologies and concepts that challenge the status quo and dogma are not welcomed, let alone promoted, or funded.
Legacy – The organization I’ve been working with, like many others, has decades of investment in existing concepts, systems, platforms, R&D labs, training, and a known set of external contractors. Building and sustaining their existing platforms and systems has left little money for creating and deploying new ones at the same scale (problems that new entrants/adversaries may not have.) Advocating that one or more of their platforms or systems are at risk or may no longer be effective is considered heresy and likely the end of a career.
The “Frozen Middle” – A common refrain I hear from innovators in large organizations is that too many people are resistant to change (“they just don’t get it”.) After seeing this behavior for decades, I’ve learned that the frozen middle occurs because of what’s called the“Semmelweis effect” – the unconscious tendency of people to stick to preexisting beliefs and reject new ideas that contradict them – because it undermines their established norms and/or beliefs. (They really don’t get it.) This group is most comfortable sticking with existing process and procedures and hires and promotes people who execute the status quo. This works well when the system can continue to succeed with incremental growth, but in the face of more radical change, this normal human reaction shuts out new learning and limits an organizations’ ability to rapidly adapt to new circumstances. The result is organizational blinders and frustrated innovators. And you end up with world-class people and organizations for a world that no longer exists.
Not everyone is affected by the Semmelweis effect. It’s often mid-grade managers / officers in this same “middle” who come up with disruptive solutions and concepts. However, unless they have senior champions (VP’s, Generals / Admirals) and are part of an organization with a mission to solve operational problems, these solutions die. These innovators lack alternate places where the culture encourages and funds experimentation and non-consensus ideas. Ironically, organizations tend to chase these employees out because they don’t conform, or if forced to conform, they grow disillusioned and leave for more innovative work in industry.
Hubris is managerial behavior of overconfidence and complacency. Unlike the unconscious Semmelweis effect, this is an active and conscious denial of facts. It occurs as some leaders/managers believe change threatens their jobs as decision-makers or that new programs, vendors or ideas increase the risk of failure, which may hurt their image and professional or promotional standing.
In the organization I’ve been working with, the internal engineering group offers senior leaders reassurances that they are responding to disruption by touting incremental upgrades to their existing platforms and systems.
Meanwhile because their budget is a zero-sum game, they starve innovators of funds and organizational support for deployment of disruptive new concepts at scale. The result is “innovation theater.” In the commercial world this behavior results in innovation demos but no shipping products and a company on the path to irrelevance or bankruptcy. In the military it’s demos but no funding for deployments at scale.
Fear of Failure/Risk Aversion – Large organizations are built around repeatable and scalable processes that are designed to be “fail safe.” Here new initiatives need to match existing budgeting, legal, HR and acquisition, processes and procedures. However, disruptive projects can only succeed in organizations that have a “safe-to-fail” culture. This is where learning and discovery happens via incremental and iterative experimentation with a portfolio of new ideas and failure is considered part of the process. “Fail safe” versus “safe-to-fail” organizations need to be separate and require different culture, different people, different development processes and risk tolerance.
Activist Investors Kill Transformation in Commercial Companies
A limit on transformation speed unique to commercial organizations is the fear of “Activist Investors.” “Activist investors” push public companies to optimize short-term profit, by avoiding or limiting major investments in new opportunities and technology. When these investors gain control of a company, innovation investments are reduced, staff is cut, factories and R&D centers closed, and profitable parts of the company and other valuable assets sold.
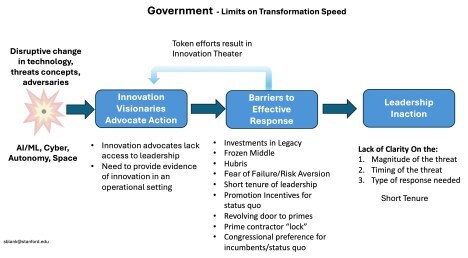
 Unique Barriers for Government Organizations
Unique Barriers for Government Organizations
Government organizations face additional constraints that make them even slower to respond to change than large companies.
To start, leaders of the largest government organizations are often political appointees. Many have decades of relevant experience, but others are acting way above their experience level. This kind of mismatch tends to happen more frequently in government than in private industry.
Leaders’ tenures are too short – All but a few political appointees last only as long as their president in the White House, while leaders of programs and commands in the military services often serve 2- or 3-year tours. This is way too short to deeply understand and effectively execute organizational change. Because most government organizations lack a culture of formal innovation doctrine or playbook – a body of knowledge that establishes a common frame of reference and common professional language – institutional learning tends to be ephemeral rather than enduring. Little of the knowledge, practices, shared beliefs, theory, tactics, tools, procedures, language, and resources that the organization built under the last leader gets forwarded. Instead each new leader relearns and imposes their own plans and policies.
Getting Along Gets Rewarded – Career promotion in all services is primarily driven by “getting along” with the status quo. This leads to things like not cancelling a failing program, not looking for new suppliers who might be cheaper/ better/ more responsive, pursuing existing force design and operating concepts even when all available evidence suggests they’re no longer viable, selecting existing primes/contractors, or not pointing out that a major platform or weapon is no longer effective. The incentives are to not take risks. Doing so is likely the end of a career. Few get promoted for those behaviors. This discourages non-consensus thinking. Yet disruption requires risk.
Revolving doors – Senior leaders leave government service and go to work for the very companies whose programs they managed, and who they had purchased systems from (often Prime contractors). The result is that few who contemplate leaving the service and want a well-paying job with a contractor will hold them to account or suggest an alternate vendor while in the service.
Prime Contractors – are one of our nation’s greatest assets while being our greatest obstacles to disruptive change. In the 20th century platforms/weapons were mostly hardware with software components. In the 21st century, platforms/weapons are increasingly software with hardware added. Most primes still use Waterfall development with distinct planning, design, development, and testing phases rather than Agile (iterative and incremental development with daily software releases). The result is that primes have a demonstrated inability to deliver complex systems on time. (Moving primes to software upgradable systems/or cloud-based breaks their financial model.)
As well, prime contractors typically have a “lock” on existing government contracts. That’s because it’s less risky for acquisition officials to choose them for follow-on work– and primes have decades of experience in working through the byzantine and complex government purchasing process; and they have tons of people and money to influence all parts of the government acquisition system—from the requirements writers to program managers, to congressional staffers to the members of the Armed Services and Appropriations committees. New entrants have little chance to compete.
Congress – Lawmakers have incentives to support the status quo but few inducements to change it. Congress has a major say in what systems and platforms suppliers get used, with a bias to the status quo. To keep their own jobs, lawmakers shape military appropriations bills to support their constituents’ jobs and to attract donations from the contractors who hire them. (They and their staffers are also keeping the revolving door in mind for their next job.) Many congressional decisions that appear in the National Defense Authorization Act (NDAA) and in appropriations are to support companies that provide the most jobs in their districts and the most funds for their reelection. These come from the Prime contractors.
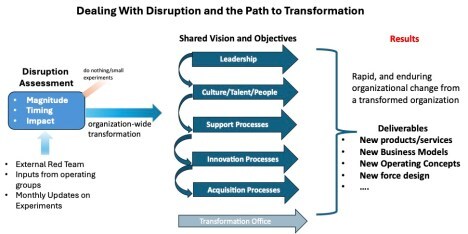
What to Do About It?
It starts at the top. Confronted with disruptive threats, senior leaders must actively work to understand:
Increase Visibility of Disruptive Tech and Concepts/Add Outside Opinions
Actively and Urgently Gather Evidence
Run real-world experiments – simulations, war games, – using disruptive tech and operating concepts (in offense and defense.)See and actively seek out the impact of disruption in adjacent areas e.g. AI’s impact on protein modeling, drones in the battlefield and Black Sea in Ukraine, et al.Ask the pointy end of the organization (e.g the sales force, fleet admirals) if they are willing to take more risk on new capabilities.These activities need happen in months not years. Possible recommendations from these groups include do nothing, run small experiments, transform a single function or department, or a company or organization-wide transformation.
What Does Organization-wide Transformation look like?
What outcome do we desire?When do we need it?What budget, people, capital equipment are needed?What would need to be divested?How to communicate this to all stakeholders and get them aligned?In the face of disruption/ crisis/ wartime advanced R&D groups now need a seat at the table with budgets sufficient for deployment at scale.Consider organizing as an ambidextrous organization (e.g. SpaceX Falcon 9 operational execution versus Starship disruptive experimentation) (see this HBR article.)In addition to mangers of process, create rapid innovation teams (technologists, visionaries, senior champions)Finally, encourage more imagination. How can we use partners and other outside resources for technology and capital?Examples of leaders who transformed their organization in the face of disruption include Microsoft CEO Satya Nadella and Steve Jobs from Apple, in defense, Bill Perry, Harold Brown and Ash Carter. Each dealt with disruption with acceptance, acknowledgment, imagination and action.
June 27, 2024
Lean LaunchPad @Stanford 2024 – 8 Teams In, 8 Companies Out
 This post previously appeared in Poets and Quants.
This post previously appeared in Poets and Quants.
We just finished the 14th annual Lean LaunchPad class at Stanford. The class had gotten so popular that in 2021 we started teaching it in both the winter and spring sessions.
During the quarter the eight teams spoke to 919 potential customers, beneficiaries and regulators. Most students spent 15-20 hours a week on the class, about double that of a normal class.
In the 14 years we’ve been teaching the class, we had something that has never happened before – all eight teams in this cohort have decided to start a company.
This Class Launched a Revolution in Teaching Entreprenurship
Several government-funded programs have adopted this class at scale. The first was in 2011 when we turned this syllabus into the curriculum for the National Science Foundation I-Corps. Errol Arkilic, the then head of commercialization at the National Science, adopted the class saying, “You’ve developed the scientific method for startups, using the Business Model Canvas as the laboratory notebook.”
Below are the Lessons Learned presentations from the spring 2024 Lean LaunchPad.
Team Neutrix – Making Existing Nuclear Reactors More Profitable By Upgrading Their FuelIf you can’t see the Neutrix video, click here
 If you can’t see the Neutrix Presentation, click here
If you can’t see the Neutrix Presentation, click here
I-Corps at the National Institute of Health
In 2013 I partnered with UCSF and the National Institute of Health to offer the Lean LaunchPad class for Life Science and Healthcare (therapeutics, diagnostics, devices and digital health.) In 2014, in conjunction with the National Institute of Health, I took the UCSF curriculum and developed and launched the I-Corps @ NIH program.
If you can’t see the Virgil video, click here
 If you can’t see the Virgil Presentation, click here.
If you can’t see the Virgil Presentation, click here.
I-Corps at Scale
I-Corps is now offered in 100 universities and has trained over 9,500 scientists and engineers; 7,800 in 2,546 teams in I-Corps at NSF (National Science Foundation), 950 participants at I-Corps at NIH in 317 teams, and 580 participants at Energy I-Corps (at the DOE) in 188 teams.
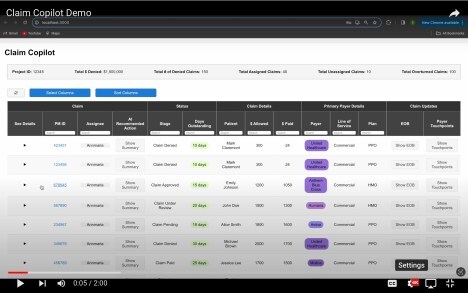
 If you can’t see the Claim Pilot Presentation, click here
If you can’t see the Claim Pilot Presentation, click here
If you can’t see the Claim CoPilot video of their demo click here
$4 billion in Venture Capital For I-Corps Teams
1,380 of the NSF I-Corps teams launched startups raising $3.166 billion. Over 300 I-Corps at NIH teams have collectively raised $634 million. Energy I-Corps teams raised $151 million in additional funding.
 If you can’t see the Emy.ai video, click here
If you can’t see the Emy.ai video, click here
 If you can’t see the Emy.ai Presentation, click here
If you can’t see the Emy.ai Presentation, click here
Mission Driven Entreprenurship
In 2016, I co-created both the Hacking for Defense course with Pete Newell and Joe Felter as well as the Hacking for Diplomacy course with Jeremy Weinstein at Stanford. In 2022, Steve Weinstein created Hacking for Climate and Sustainability. This fall Jennifer Carolan will launch Hacking for Education at Stanford.
If you can’t see the TeachAssist video, click here
 If you can’t see the TeachAssist Presentation, click here
If you can’t see the TeachAssist Presentation, click here
Design of This Class
While the Lean LaunchPad students are experiencing what appears to them to be a fully hands-on, experiential class, it’s a carefully designed illusion. In fact, it’s highly structured. The syllabus has been designed so that we are offering continual implicit guidance, structure, and repetition. This is a critical distinction between our class and an open-ended experiential class.
Guidance, Direction and Structure
For example, students start the class with their own initial guidance – they believe they have an idea for a product or service (Lean LaunchPad/I-Corps) or have been given a clear real-world problem (Hacking for Defense). Coming into the class, students believe their goal is to validate their commercialization or deployment hypotheses. (The teaching team knows that over the course of the class, students will discover that most of their initial hypotheses are incorrect.)
If you can’t see the Maurice.ai video, click here
 If you can’t see the Maurice.ai Presentation, click here
If you can’t see the Maurice.ai Presentation, click here
The Business Model Canvas
The business/mission model canvas offers students guidance, explicit direction, and structure. First, the canvas offers a complete, visual roadmap of all the hypotheses they will need to test over the entire class. Second, the canvas helps the students goal-seek by visualizing what an optimal endpoint would look like – finding product/market fit. Finally, the canvas provides students with a map of what they learn week-to-week through their customer discovery work.
I can’t overemphasize the important role of the canvas. Unlike an incubator or accelerator with no frame, the canvas acts as the connective tissue – the frame – that students can fall back on if they get lost or confused. It allows us to teach the theory of how to turn an idea, need, or problem into commercial practice, week by week a piece at a time.
Team Waifinder – Personalized Guidance For High School Students to Effectively Apply to CollegeIf you can’t see the Waifinder video, click here
 If you can’t see the Waifinder Presentation, click here
If you can’t see the Waifinder Presentation, click here
Lean LaunchPad Tools
The tools for customer discovery (videos, sample experiments, etc.) offer guidance and structure for students to work outside the classroom. The explicit goal of 10-15 customer interviews a week along with the requirement for building a continual series of minimal viable products provides metrics that track the team’s progress. The mandatory office hours with the instructors and support from mentors provide additional guidance and structure.
 If you cant see the PocketDot video click here.
If you cant see the PocketDot video click here.
 If you can’t see the PocketDot Presentation, click here
If you can’t see the PocketDot Presentation, click here
It Takes A Village
While I authored this blog post, this class is a team project. The secret sauce of the success of the Lean LaunchPad at Stanford is the extraordinary group of dedicated volunteers supporting our students in so many critical ways.
The teaching team consisted of myself and:
Steve Weinstein, partner at America’s Frontier Fund, 30-year veteran of Silicon Valley technology companies and Hollywood media companies. Steve was CEO of MovieLabs, the joint R&D lab of all the major motion picture studios.Lee Redden – CTO and co-founder of Blue River Technology (acquired by John Deere) who was a student in the first Lean LaunchPad class 14 years ago!Jennifer Carolan, Co-Founder, Partner at Reach Capital the leading education VCShawn Carolan Partner at Menlo Ventures.Our teaching assistants this year were Chapman Ellsworth, Francesca Bottazzini and Ehsan Ghasemi.
Mentors helped the teams understand if their solutions could be a commercially successful business. Thanks to Lofton Holder, Bobby Mukherjee, Steve Cousins, David Epstein, Kevin Ray, Rekha Pai, Rafi Holtzman and Kira Makagon. They were led by Todd Basche.
Summary
While the Lean LaunchPad/I-Corps curriculum was a revolutionary break with the past, it’s not the end. In the last decade enumerable variants have emerged. The class we teach at Stanford has continued to evolve. Better versions from others will appear. AI is already having a major impact on customer discovery and validation. And one day another revolutionary break will take us to the next level.
But today, we get to celebrate – 8 teams in – 8 companies out.
June 24, 2024
Hacking for Defense @ Stanford 2024 – Lessons Learned Presentations
We just finished our 9th annual Hacking for Defense class at Stanford.
What a year.
Hacking for Defense, now in 60 universities, has teams of students working to understand and help solve national security problems. At Stanford this quarter the 8 teams of 40 students collectively interviewed 968 beneficiaries, stakeholders, requirements writers, program managers, industry partners, etc. – while simultaneously building a series of minimal viable products and developing a path to deployment.
At the end of the quarter, each of the teams gave a final “Lessons Learned” presentation. Unlike traditional demo days or Shark Tanks which are, “Here’s how smart I am, and isn’t this a great product, please give me money,” the Lessons Learned presentations tell the story of each team’s 10-week journey and hard-won learning and discovery. For all of them it’s a roller coaster narrative describing what happens when you discover that everything you thought you knew on day one was wrong and how they eventually got it right.
Here’s how they did it and what they delivered.
New for 2024
This year, in addition to the problems from the Defense Department and Intelligence Community we had two problems from the State Department and one from the FBI.
These are “Wicked” Problems
Wicked problems refer to really complex problems, ones with multiple moving parts, where the solution isn’t obvious and lacks a definitive formula. The types of problems our Hacking For Defense students work on fall into this category. They are often ambiguous. They start with a problem from a sponsor, and not only is the solution unclear but figuring out how to acquire and deploy it is also complex. Most often students find that in hindsight the problem was a symptom of a more interesting and complex problem – and that Acquistion of solutions in the Dept of Defense is unlike anything in the commercial world.
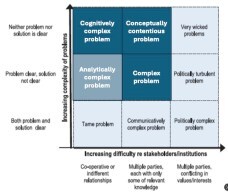 And the stakeholders and institutions often have different relationships with each other – some are collaborative, some have pieces of the problem or solution, and others might have conflicting values and interests.
And the stakeholders and institutions often have different relationships with each other – some are collaborative, some have pieces of the problem or solution, and others might have conflicting values and interests.
The figure shows the types of problems Hacking for Defense students encounter, with the most common ones shaded.
Guest Speakers: Doug Beck – Defense Innovation Unit, Radha Plumb – CDAO. H.R. McMaster – former National Security Advisor and Condoleezza Rice – former Secretary of State
Our final Lessons Learned presentations started with an introduction by Doug Beck, director of the Defense Innovation Unit and Radha Plumb, DoD’s Chief of the Digital and AI Office– reminding the students of the importance of Hacking for Defense and congratulating them on their contribution to national security.
H.R. McMaster gave an inspiring talk. He reminded our students that 1) war is an extension of politics; 2) war is human; 3) war is uncertain; 4) war is a contest of wills.
If you can’t see the video of H.R. McMaster’s talk, click here.
The week prior to our final presentations the class heard inspirational remarks from Dr. Condoleezza Rice, former United States Secretary of State. Dr. Rice gave a sweeping overview of the prevailing threats to our national security and the importance of getting our best and brightest involved in public service.
As a former Secretary of State, Dr. Rice was especially encouraged to see our two State Department sponsored teams this quarter. She left the students inspired to find ways to serve.
Lessons Learned Presentation Format
For the final Lessons Learned presentation many of the eight teams presented a 2-minute video to provide context about their problem. This was followed by an 8-minute slide presentation describing their customer discovery journey over the 10 weeks. While all the teams used the Mission Model Canvas, (videos here), Customer Development and Agile Engineering to build Minimal Viable Products, each of their journeys was unique.
By the end the class all the teams realized that the problem as given by the sponsor had morphed into something bigger, deeper and much more interesting.
All the presentations are worth a watch.
Team House of LawsUsing LLMs to Simplify Government Decision Making
If you can’t see the Team House of Laws 2-minute video, click here
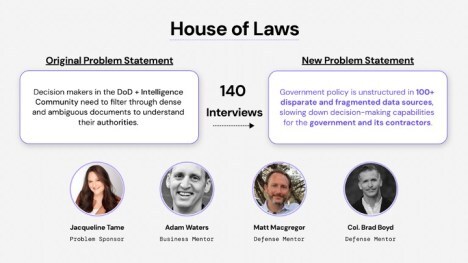 If you can’t see the Team House of Laws slides, click here
If you can’t see the Team House of Laws slides, click here
Mission-Driven Entrepreneurship
This class is part of a bigger idea – Mission-Driven Entrepreneurship. Instead of students or faculty coming in with their own ideas, we ask them to work on societal problems, whether they’re problems for the State Department or the Department of Defense or non-profits/NGOs or the Oceans and Climate or for anything the students are passionate about. The trick is we use the same Lean LaunchPad / I-Corps curriculum — and the same class structure – experiential, hands-on– driven this time by a mission-model not a business model. (The National Science Foundation and the Common Mission Project have helped promote the expansion of the methodology worldwide.)
Mission-driven entrepreneurship is the answer to students who say, “I want to give back. I want to make my community, country or world a better place, while being challenged to solve some of the toughest problems.”
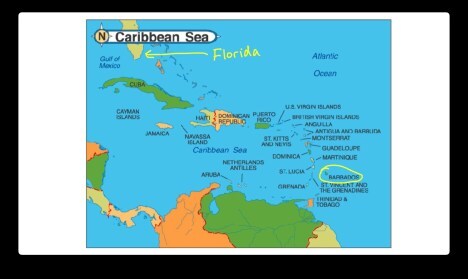
Caribbean Clean ClimateHelping Barbados Adopt Clean Energy
If you can’t see the Caribbean Clean Climate 2-minute video, click here
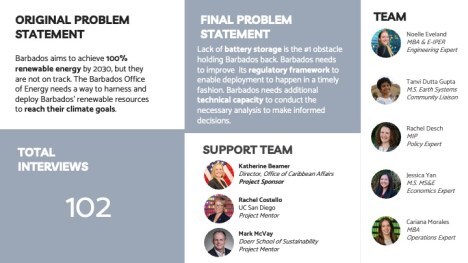 If you can’t see the Caribbean Clean Climate slides, click here
If you can’t see the Caribbean Clean Climate slides, click here
It Started With An Idea
Hacking for Defense has its origins in the Lean LaunchPad class I first taught at Stanford in 2011. I observed that teaching case studies and/or how to write a business plan as a capstone entrepreneurship class didn’t match the hands-on chaos of a startup. Furthermore, there was no entrepreneurship class that combined experiential learning with the Lean methodology. Our goal was to teach both theory and practice.
The same year we started the class, it was adopted by the National Science Foundation to train Principal Investigators who wanted to get a federal grant for commercializing their science (an SBIR grant.) The NSF observed, “The class is the scientific method for entrepreneurship. Scientists understand hypothesis testing” and relabeled the class as the NSF I-Corps (Innovation Corps). I-Corps became the standard for science commercialization for the National Science Foundation, National Institutes of Health and the Department of Energy, to date training 3,051 teams and launching 1,300 startups.
Team Protecting ChildrenHelping the FBI Acquire LLMs for Child Safety
If you can’t see the Team Protecting Children 2-minute video, click here
 If you can’t see the Team Protecting Children slides, click here
If you can’t see the Team Protecting Children slides, click here
Origins Of Hacking For Defense
In 2016, brainstorming with Pete Newell of BMNT and Joe Felter at Stanford, we observed that students in our research universities had little connection to the problems their government was trying to solve or the larger issues civil society was grappling with. As we thought about how we could get students engaged, we realized the same Lean LaunchPad/I-Corps class would provide a framework to do so. That year we launched both Hacking for Defense and Hacking for Diplomacy (with Professor Jeremy Weinstein and the State Department) at Stanford. The Department of Defense adopted and scaled Hacking for Defense across 60 universities while Hacking for Diplomacy is offered at JMU and RIT –, sponsored by the Department of State Bureau of Diplomatic Security (see here).
Improving Satellite Tasking
If you can’t see the Team L∞ 2-minute video, click here
 If you can’t see the Team L∞ slides, click here
If you can’t see the Team L∞ slides, click here
Goals for the Hacking for Defense Class
Our primary goal was to teach students Lean Innovation methods while they engaged in national public service. Today if college students want to give back to their country, they think of Teach for America, the Peace Corps, or AmeriCorps or perhaps the US Digital Service or the GSA’s 18F. Few consider opportunities to make the world safer with the Department of Defense, Intelligence community or other government agencies.
In the class we saw that students could learn about the nation’s threats and security challenges while working with innovators inside the DoD and Intelligence Community. At the same time the experience would introduce to the sponsors, who are innovators inside the Department of Defense (DOD) and Intelligence Community (IC), a methodology that could help them understand and better respond to rapidly evolving threats. We wanted to show that if we could get teams to rapidly discover the real problems in the field using Lean methods, and only then articulate the requirements to solve them, defense acquisition programs could operate at speed and urgency and deliver timely and needed solutions.
Finally, we wanted to familiarize students with the military as a profession and help them better understand its expertise, and its proper role in society. We hoped it would also show our sponsors in the Department of Defense and Intelligence community that civilian students can make a meaningful contribution to problem understanding and rapid prototyping of solutions to real-world problems.
Team CentimentInformation Operations Optimized
If you can’t see the Team Centiment 2-minute video, click here
 If you can’t see the Team Centiment slides, click here
If you can’t see the Team Centiment slides, click here
Mission-Driven in 50 Universities and Continuing to Expand in Scope and Reach
What started as a class is now a movement.
From its beginning with our Stanford class, Hacking for Defense is now offered in over 50 universities in the U.S., as well as in the UK and Australia. Steve Weinstein started Hacking for Impact (Non-Profits) and Hacking for Local (Oakland) at U.C. Berkeley, and Hacking for Oceans at both Scripps and UC Santa Cruz, as well as Hacking for Climate and Sustainability at Stanford. Hacking for Education will start this fall at Stanford.
Team Guyana’s Green GrowthWater Management for Guyanese Farmers
Screenshot
If you can’t see the Team Guyana’s Green Growth 2-minute video, click here
 If you can’t see the Team Guyana’s Green Growth slides, click here
If you can’t see the Team Guyana’s Green Growth slides, click here
Go-to-Market/Deployment Strategies
The initial goal of the teams is to ensure they understand the problem. The next step is to see if they can find mission/solution fit (the DoD equivalent of commercial product/market fit.) But most importantly, the class teaches the teams about the difficult and complex path of getting a solution in the hands of a warfighter/beneficiary. Who writes the requirement? What’s an OTA? What’s color of money? What’s a Program Manager? Who owns the current contract? …
Cubesats for Space Inspection Training

Screenshot
If you can’t see the Team Dynamic Space Operations 2-minute video, click here
 If you can’t see the Team Dynamic Space Operations slides, click here
If you can’t see the Team Dynamic Space Operations slides, click here
Providing real-time awareness of ..
This team’s presentation is available upon request.
If you can’t see the Spectra Labs slides, click here
What’s Next For These Teams?
When they graduate, the Stanford students on these teams have the pick of jobs in startups, companies, and consulting firms. House of Laws got accepted and has already started at Y-Combinator. L-Infinity, Dynamics Space Operations team (now Juno Astrodynamics,) and Spectra Labs are started work this week at H4X Labs, an accelerator focused on building dual-use companies that sell to both the government and commercial firms. Many of the teams will continue to work with their problem sponsor. Several will join the Stanford Gordian Knot Center for National Security Innovation which is focused on the intersection of policy, operational concepts, and technology.
In our post class survey 86% of the students said that the class had impact on their immediate next steps in their career. Over 75% said it changed their opinion of working with the Department of Defense and other USG organizations.
It Takes A Village
While I authored this blog post, this class is a team project. The secret sauce of the success of Hacking for Defense at Stanford is the extraordinary group of dedicated volunteers supporting our students in so many critical ways.
The teaching team consisted of myself and:
Pete Newell, retired Army Colonel and ex Director of the Army’s Rapid Equipping Force, now CEO of BMNT.Joe Felter, retired Army Colonel; and former deputy assistant secretary of defense for South Asia, Southeast Asia, and Oceania; and William J. Perry Fellow at Stanford’s Center for International Security and Cooperation.Steve Weinstein, partner at America’s Frontier Fund, 30-year veteran of Silicon Valley technology companies and Hollywood media companies. Steve was CEO of MovieLabs, the joint R&D lab of all the major motion picture studios. He runs H4X Labs.Jeff Decker, a Stanford researcher focusing on dual-use research. Jeff served in the U.S. Army as a special operations light infantry squad leader in Iraq and Afghanistan. Our teaching assistants this year were Joel Johnson, Malika Aubakirova, Spencer Paul, Ethan Tiao, Evan Szablowski, and Josh Pickering. A special thanks to the Defense Innovation Unit (DIU) and its National Security Innovation Network (NSIN) for supporting the program at Stanford and across the country, as well as Lockheed Martin and Northrop Grumman.
Our teaching assistants this year were Joel Johnson, Malika Aubakirova, Spencer Paul, Ethan Tiao, Evan Szablowski, and Josh Pickering. A special thanks to the Defense Innovation Unit (DIU) and its National Security Innovation Network (NSIN) for supporting the program at Stanford and across the country, as well as Lockheed Martin and Northrop Grumman.
31 Sponsors, Business and National Security Mentors
The teams were assisted by the originators of their problems – the sponsors.
Thanks to all!
June 3, 2024
You’re Invited: Hacking for Defense and Lean LaunchPad Final Presentations
Join us for the final presentations of our two Stanford classes this Tuesday June 4th and Wednesday June 5th.
Tuesday = Hacking for Defense
Wednesday = Lean Launchpad
The presentations just get better every year. Attend in person or via Zoom.
This year AI seems to be part of almost every team.
Zoom link and RSVP for Hacking for Defense here Zoom link and RSVP for Lean LaunchPad here
Zoom link and RSVP for Lean LaunchPad here
May 26, 2024
Gordon Bell R.I.P.
Gordon Bell passed on this month.
I was a latecomer in Gordon Bell’s life. But he made a lasting impact on mine.
The first time I laid eyes on Gordon Bell was in 1984 outside a restaurant in a Boston suburb when he pulled up in a Porsche. I was the head of Marketing for MIPS Computer, a RISC chip startup. The entire company (all of five of us) were out visiting the east coast to meet Prime Computer who would become our first major customer. (When Gordon was CTO of Encore Computer he encouraged the MIPS founders to start the company, thinking they could provide the next processor for his Multimax computer.)
My West Coast centric world of computing had been limited to custom bit-sliced computers, HP 2100 and 21MX, Interdata 8/32 minicomputers and Zilog microprocessors. Gordon was already a legend – as VP of Research and Development at Digital Equipment Corporation (DEC) he designed some of the early minicomputers and oversaw the creation of the VAX 11-780. His work at DEC revolutionized the computing industry, making powerful computing accessible.
Even so, as we talked over dinner at first I couldn’t understand a word he was saying, until I realized that he had three or four levels of conversation going simultaneously, all interleaved. If you could keep them sorted it was fun to keep up with each thread. By dessert I became another member of the Gordon Bell fan club.
Two years later, on a lunch break in downtown Palo Alto I ran into Gordon again. He was out to attend a Teknowledge board meeting. I invited him over to meet the founding team of Ardent, our new startup, whose founders he knew from DEC. By the end of the day Gordon had joined our team as founding VP of Engineering and another phase in my education was about to begin.
As an entrepreneur in my 20’s and 30’s, I was lucky to have four extraordinary mentors, each brilliant in his own field and each a decade or two older than me. While others taught me how to think, it was Gordon Bell who taught me what to think about. He could see the destination clearer than anyone I’ve ever met. The best part of my day was hearing him tell me about 3 ideas at a time and me do the same back to him. He had an extraordinary instinct for guiding me away from the purely dumb paths that would lead nowhere and nudge me on to the more productive roads. (He had this warm laugh, a kind of a chuckle when he was listening to some of more dumber ideas.)
At Digital Equipment Gordon had developed a heuristic that attempted to predict the evolution of the next class of computers. And when he left DEC he created the Bell-Mason diagnostic to help predict patterns in successful startups. The idea that there was a pattern about startup success and failure would stick in the back of my head for decades and shape the second half of my career. And as he was brainstorming about some of the early ideas about what became his MyLifeBits project I was inspired to start a small version of my own.
For the next 15 years Gordon would help me understand how to think critically about the possibilities over the horizon. Yet at the same time Gordon was looking forward, he was teaching us to respect and learn from the past.
Gordon and his wife Gwen started a computer history museum and by 1983 moved it into renovated warehouse next to the Boston Children’s Museum. In 1986 I spent two weeks making a short movie about the history of high-performance computing at the museum. Gordon and Gwen put me up in their guest bedroom overlooking Boston Harbor and a short walk across the Congress Street bridge to the museum. This not only began my long-term love affair with the museum but also made me realize that computer history and the history of innovation clusters were missing the story of how the military and intelligence community had shaped the trajectory of post WWII technology.
Seven years later, in my next startup, I would end up in their apartment again, this time with my wife and two young daughters, to attend the MacWorld trade show. I vividly remember the girls running around their living room decorated with many of the artifacts the museum didn’t have room to display (with Gwen patiently telling them that the Arithmometer and Napier’s Bones weren’t toys.) For the next few years, we’d return (with the artifacts safely hidden away.)
By the time I started my final startup Epiphany, Gordon was at Microsoft, and he became my most valuable advisor.
Gordon was not only a mentor and inspiration to me, but to countless engineers and computer scientists. It was a privilege to know him.

2004
I’ll miss him.
May 21, 2024
The Venture Mindset – Worth A Read
Ilya Strebulaev at the Stanford Graduate School of Business and Director of the Stanford Venture Capital Initiative just came out with a book that should be on your reading list – The Venture Mindset.
The books premise is that Venture Capitalists (who were responsible for the launch of one-fifth of the 300 largest U.S. public companies) have a different mindset then that found in the rest of the business world (and I would add in government agencies.) All these startups could have come from inside an existing company—but they didn’t.
The book answers why that’s so. And why are venture firms good at finding start-ups that turn into unicorns – what are the skills that VC firms have that companies don’t? And most importantly, can you/your company learn those skills?
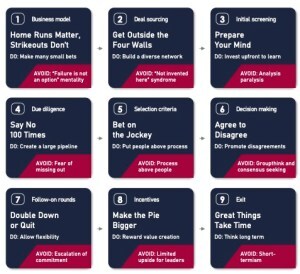
The Venture Mindset is built around 9 key ideas:
If you’re a founder looking to raise capital, this book will help you understand how VC’s are evaluating your company. (I wish I had read this book at the beginning of my entrepreneurial journey.)
If you’re in a large company or government agency this book will help you understand the difference between “fail-safe” bets needed in sustaining the core business, versus “safe-to-fail” bets, needed in creating new businesses and/or disruptive capabilities.
Definitely worth a read.
Steve Blank's Blog
- Steve Blank's profile
- 380 followers